Openssl Key Generation Gui For Windows
- Openssl Key Generation Gui For Windows 7
- Openssl Download Windows 64
- Install Openssl Windows Server 2012
- Openssl For Windows
Version 1.3
Here's an example of how to generate Secure Boot keys (PK and others) by using a hardware security module (HSM).
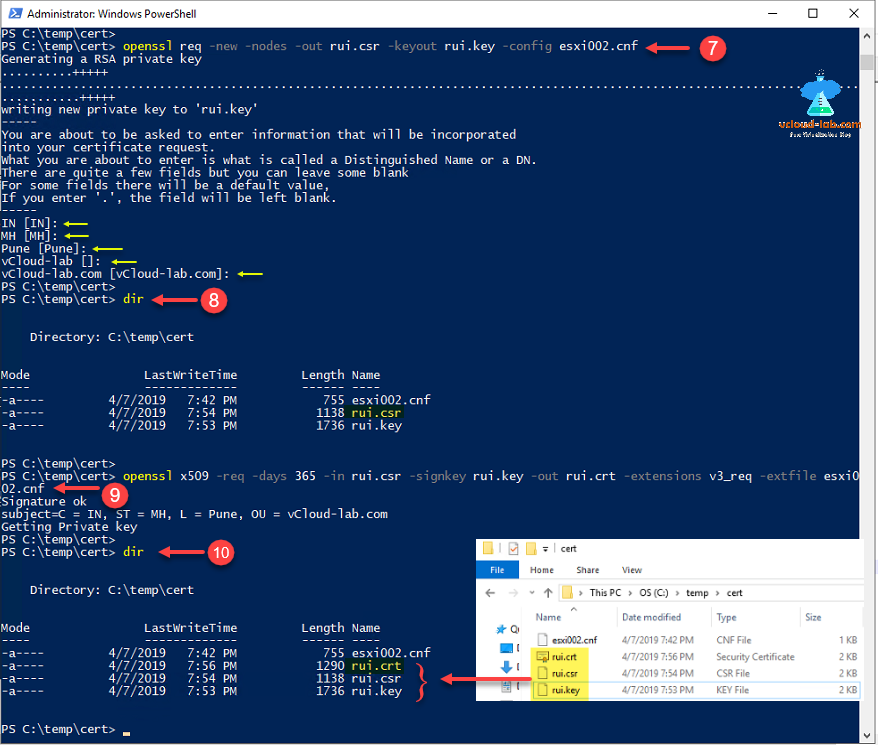
To generate a hash of your release key, run the following command on Mac or Windows substituting your release key alias and the path to your keystore. On Windows, use: keytool -exportcert -alias KEYALIAS -keystore KEYPATH openssl sha1 -binary openssl base64 This command should generate a 28 characher string. Download OpenSSLUI,OpenSSL UI,OpenSSLGUI for free. This project is intended to create a free Windows based UI for command line openssl operations. Currently a UI has been developed with Windows WPF. Update: if you don’t have access to a machine with OpenSSL, I created a website to generate certs using the procedure described here. Read through the procedure, and then use the website listed at the end. Host key generation Public keys have specific ACL requirements that, on Windows, equate to only allowing access to administrators and System. To make this easier, The OpenSSHUtils PowerShell module has been created to set the key ACLs properly, and should be installed on the server.
You'll need to know the Secure Boot Public Key Infrastructure (PKI). For more info, see Windows 8.1 Secure Boot Key Creation and Management Guidance.
Requirements
Openssl Key Generation Gui For Windows 7
Tools Needed
certreq.exe – Available Inbox
certutil.exe – Available Inbox
Signtool.exe – Available in the latest Windows SDK
Hardware Security Module (HSM)
The whitepaper demonstrates the key generation using examples from the nCipher (now Thales) PCI HSM model nC1003P/nC3023P/nC3033P and the SafeNet Luna HSMs. Most of the concepts apply to other HSM vendors as well.
For other HSMs, contact your manufacturer for additional instructions on how to tailor your approach with the HSM Cryptographic Service Provider (CSP).
Approach
We use the Microsoft certificate creation tool: certreq.exe to generate the Secure Boot Platform Key (PK) and other keys needed for Secure Boot.
The certreq tool can be adapted to use an HSM by providing the Cryptographic Service Provider (CSP) to be the HSM.
Find the Cryptographic Service Provider (CSP)
You can use either the certutil.exe tool or a tool used by the HSM to list the CSPs.
This example uses the certutil tool to show the CSPs on the Thales/nCipher HSM:
For the SHA-256 digesting algorithm, use the CNG provider:
'nCipher Security World Key Storage Provider'. Legacy providers do not support SHA-256 and are not suitable for use with Secure Boot.This example uses the built-in Thales/nCipher tool to list the CSP:
For the SHA-256 digesting algorithm, use the CNG provider:
'nCipher Security World Key Storage Provider'. Legacy providers do not support SHA-256 and are not suitable for use with Secure Boot.This example uses the SafeNet Luna HSMs tool to list the CSP:
For SHA-256 digest algorithm you will need to use a CNG provider – “SafeNet Key Storage Provider”. Legacy providers do not support SHA-256 and are not suitable for use with Secure Boot.
To generate the key:
Sample request.inf file:
Update the following values:
Subject: Replace the TODO’s with real data
'CN=Corporation TODO Platform Key,O=TODO Corporation,L=TODO_City,S=TODO_State,C=TODO_Country'.ValidityPeriod, ValidityPeriodUnits: Use the validity period of 6 years. While a PK may only be valid for 2 years, the 6-year period allows for potential future servicing.
KeyContainer: Enter the container id that you used to create the Key with the HSM. You may be asked to provide the tokens that you have used to create the Security World for the Thales HSM.
Validating certificate (self-signed)
Verify that the certificate has been generated correctly:
For example: certutil -store -v my '7569d364a2e77b814274c81ae6360ffe'
Sample output:
Backing up the certificate
Back up your certificates. This way, if either the certificate store or the server goes down, you can add the certificate back to the store. For more info on certreq.exe, see Advanced Certificate Enrollment and Management: Appendix 3: Certreq.exe Syntax
Note, the PK is a self-signed certificate, and is also used to sign the KEK.
There are 2 parts to PK signing / initial provisioning. Please talk to your Microsoft contact to get these scripts:
subcreate_set_PK_example_initial_provisioning_example.ps1. Used by the signtool to sign the PK comes later in the servicing case.subcreate_set_PK_service_example.ps1. Since we are dealing with the HSM case, the following line applies in the script applies.
Signing with PK certificate (servicing scenario)
This section applies to signing with your PK certificate and may not be applicable for initial provisioning of system. However, you can use the method here to test your service scenario.
Determine the certificate hash (sha1)
Determine the SHA1 hash of the certificate. You can get the SHA1 hash by using either of the following methods:
In Windows, open the Certificate file, select the Details tab, and check the value for Thumbprint.
Or use the following command:
Sample output:
Sign with signtool with the certificate store specified as a reference
Use the SHA1 hash to sign the KEK certificate:
Where KEK.bin is the filename of the binary certificate you want to sign.
Sample output:
NOTE For compatibility with the UEFI Specification and maximum compatibility across UEFI implementations, the /p7co and /p7ce parameters must be present, the value passed to /p7co must be 1.2.840.113549.1.7.1, and the value passed to /p7ce must be DetachedSignedData. Also, for improved compatibility with production signing environments, a signtool.exe commandline that fully specifies the hardware key container is as follows:
For more info, see Sign Tool (SignTool.exe) and Windows 8.1 Secure Boot Key Creation and Management Guidance.
Appendix A – Using Thales KeySafe for viewing keys
Thales KeySafe is based on a GUI.
To use KeySafe, you must have installed JRE/JDK 1.4.2, 1.5, or 1.6. Install Java before you install the nCipher software.
Configure the hardserver config file under the %NFAST_KMDATA%config folder:
Edit settings in the server_startup section:
nonpriv_port. This field specifies the port on which the hardserver listens for local non-privileged TCP connections.
Default to connecting to port 9000.
If the
NFAST_SERVER_PORTenvironment variable is set, it overrides any value set for nonpriv_port
priv_port. This field specifies the port on which the hardserver listens for local privileged TCP connections.
Default to connecting to port 9001.
If the
NFAST_SERVER_PRIVPORTenvironment variable is set, it overrides any value set for priv_port
The following are screenshots from the Thales KeySafe GUI:
The following image is generated by launching the KeySafe utility and then navigating to the KeyList menu.
/lennie-tristano-transcriptions-pdf-file.html. For more info, see the nCipher/Thales Users Guide.
Appendix B: Using SafeNet CMU Utility to view keys
For more details, please consult the SafeNet Luna HSM documentation.
Related topics
- Related Questions & Answers
- Selected Reading
OpenSSL is a CLI (Command Line Tool) which can be used to secure the server to generate public key infrastructure (PKI) and HTTPS. This article helps you as a quick reference to understand OpenSSL commands which are very useful in common, and for everyday scenarios especially for system administrators.
Certificate Signing Requests (CSRs)
If we want to obtain SSL certificate from a certificate authority (CA), we must generate a certificate signing request (CSR). A CSR consists of mainly the public key of a key pair, and some additional information. Both these components are merged into the certificate whenever we are signing for the CSR.
While generating a CSR, the system will prompt for information regarding the certificate and this information is called as Distinguished Name (DN). The important field in the DN is the Common Name (CN) which should be the FQND (Fully Qualified Domain Name) of the server or the host where we intend to use the certificate with.
The next item in a DN is to provide the additional information about our business or organization. If we purchase an SSL certificate from a certificate authority (CA), it is very important and required that these additional fields like “Organization” should reflect your organization for details.
Here is a general example for the CSR information prompt, when we run the OpenSSL command to generate the CSR.
We can also provide the information by non-interactive answers for the CSR information generation, we can do this by adding the –subj option to any OpenSSL commands that we try to generate or run.
Below is an example for the –subj option where we can provide the information of the organization where we want to use this CSR.
Generating CSRs
In this section, we will cover about OpenSSL commands which are related to generating the CSR. This CSR can be used to request an SSL certificate from a certificate authority.
Generate a Private Key and a CSR
If we want to use HTTPS (HTTP over TLS) to secure the Apache or Nginx web servers (using a Certificate Authority (CA) to issue the SSL certificate). Also, the ‘.CSR’ which we will be generating has to be sent to a CA for requesting the certificate for obtaining CA-signed SSL.
Below is the command to create a 2048-bit private key for ‘domain.key’ and a CSR ‘domain.csr’ from the scratch.
The ‘–newkey rsa:2048’ is the option which we are specifying that the key should be 2048-bit using the RSA algorithm. The ’ –nodes’ option is to specifying that the private key should not be encrypted with a pass phrase. The ‘-new’ option, indicates that a CSR is being generated.
Generate a CSR from an Existing Private Key
Here we will learn about, how to generate a CSR for which you have the private key.
Below is the command to create a new .csr file based on the private key which we already have.
Generate a CSR from an Existing Certificate and Private key
Here we can generate or renew an existing certificate where we miss the CSR file due to some reason. Here, the CSR will extract the information using the .CRT file which we have.
Openssl Download Windows 64
Below is the example for generating –
Where -x509toreq is specified that we are using the x509 certificate files to make a CSR.
Generating a Self-Singed Certificates
Here we will generate the Certificate to secure the web server where we use the self-signed certificate to use for development and testing purpose.
Install Openssl Windows Server 2012
Here, we generate self-signed certificate using –x509 option, we can generate certificates with a validity of 365 days using –days 365 and a temporary .CSR files are generated using the above information.
Viewing the Certificates Files
Please note that, CSR files are encoded with .PEM format (which is not readable by the humans). This is required to view a certificate. In this section, we can cover the OpenSSL commands which are encoded with .PEM files.
Viewing CSR Files Entires
The below command will be used to view the contents of the .CRT files Ex (domain.crt) in the plain text format.
Working with Private Keys
In this section, will see how to use OpenSSL commands that are specific to creating and verifying the private keys.
Create a Private Key
Below is the command to create a password-protected and, 2048-bit encrypted private key file (ex. domain.key) –
Enter a password when prompted to complete the process.
Verify a Private Key
Below is the command to check that a private key which we have generated (ex: domain.key) is a valid key or not
If the private key is encrypted, you will be prompted to enter the pass phrase. Upon the successful entry, the unencrypted key will be the output on the terminal.
Openssl For Windows
In this article, we have learnt some commands and usage of OpenSSL commands which deals with SSL certificates where the OpenSSL has lots of features. We will learn more features and usage in the future. I hope this article will help us to understand some basic features of the OpenSSL.